Setting Up a Lab
DCPromo has come a long way in the past 13 + years. Windows Server all up is so incredibly different, more powerful, more intuitive, more manageable. It is simply a great operating system to work with. I have a very specific scenario that I want to talk about here. That is setting up a lab.
There are many ways to do this, and they all have their benefits. I want to start simply. The first machine in the lab, setup as the forest root, your first DC.
The Scenario
This is not simply building a new lab. This is the re-building process that many of us go through every couple of months to get a clear setup to test with. Building the lab manually is a powerful experience especially when you are being introduced to a new OS. In this case I’m running Windows Server 2012 R2. I want to walk through the creation process manually to see if anything noticeable has changed. In this case I have already installed the Active Directory Domain Services Role and now it needs to be configured. This is the DCPromo process we have used for years. The task is initiated from within Server Manager.
After you install the AD DS role you will notice a flag informing you that you now need to ‘promote’ this server to function as a Domain Controller.

Click ‘Promote this server to a domain controller’ and the ‘Deployment Configuration’ Wizard will start.
The purpose of this post is not to walk through the configuration of the domain. In summary you can add a new DC to a domain, add a new domain or create a new forest. I’m going to create a new forest.
After walking through basic configuration, naming your domain, DC options, functional levels, NetBIOS naming, paths to files etc. etc. etc. You will come to a page in the wizard called ‘Review Options’. Along the way there are lots of links to additional information. If you are new to AD or new to Windows Server 2012 R2, take the time to read this information. It will save you time in the future.
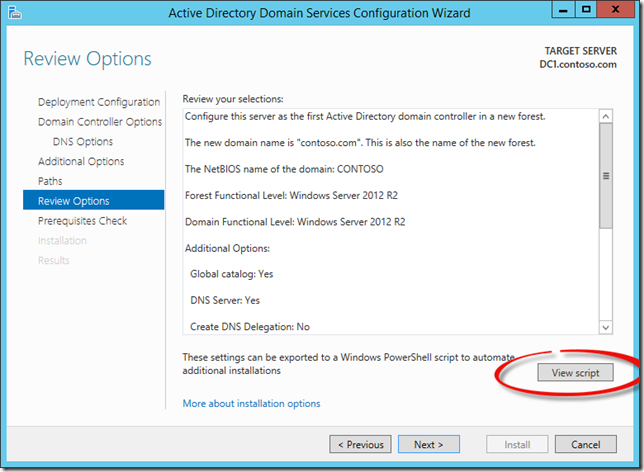
Notice the ‘View script’ button in the bottom of the dialog. Hmmm… what could that be?

A simple PowerShell script to configure your first DC. You don’t need to, or want to, run the wizard every time you need to rebuild your lab. Simply save this script as a .ps1 file. Save it in a place that you will keep to use every time you build out a new lab.
I am going to cancel the wizard after I save the script. I want to execute this DC Promotion in PowerShell. I like to use the PowerShell ISE for multiple reasons but when working with scripts you have both the scripting windows right along with the console. Makes things very easy.
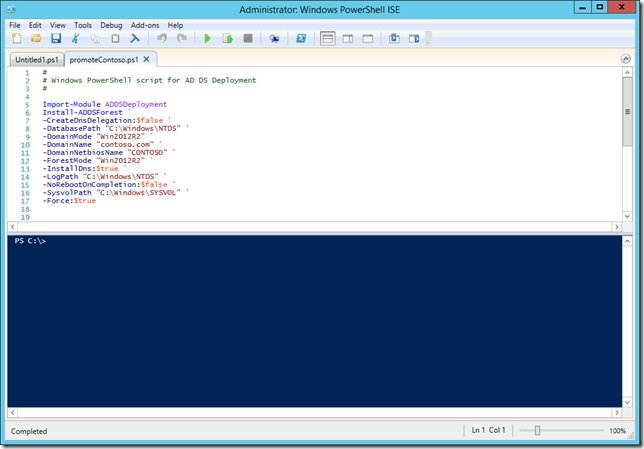
You can hit F5 or click the green arrow or get into the ‘Debug’ menu for more options. For the quick and dirty I’m just clicking the green arrow. Provide your SafeModeAdministratorPassword and off it goes.

You may get some messages and warning along the way. PowerShell seems to provide great feedback to help you understand what is going on.
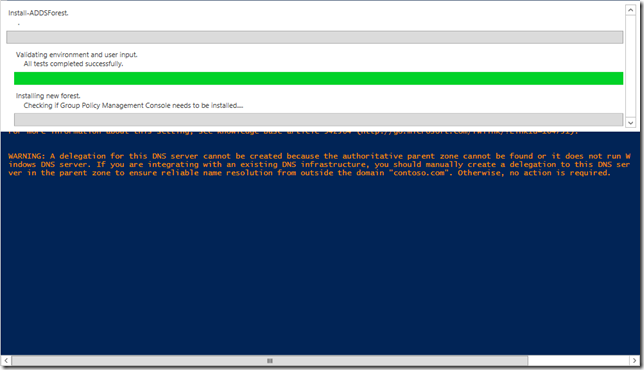
The server will reboot and your DC is setup.
Save the script, store it. You will find many others. I will explore Desired State Configuration (DSC) in the future to really fully leverage PowerShell to manage deployment and configuration of components across your enterprise. I have a long way to go before I’m ready for that! Just getting my feet wet with DSC at this point.
Enjoy!















